Updated April 4, 2023.
Identity theft. Ransomware. Data breach. Malware. Brute-force attack. If you’re familiar with any of these terms, chances are your stomach hurts just reading them.
But being afraid doesn’t stop them from happening.
With each passing year, security threats grow stronger, targeting more businesses. What are cybercriminals looking for? Credentials.
In its DBIR: 2021 Data Breach Investigations Report, Verizon found that usernames and passwords (i.e., credentials) account for about 60% of sought-after data in a security breach. On top of that, money is the motive in nearly 75% of incidents across all industries.
Simply put, criminals are actively attacking networks on a daily basis for financial gain, and none of us are immune.
Today, we'll be tackling the front line of security: secure password creation and management.
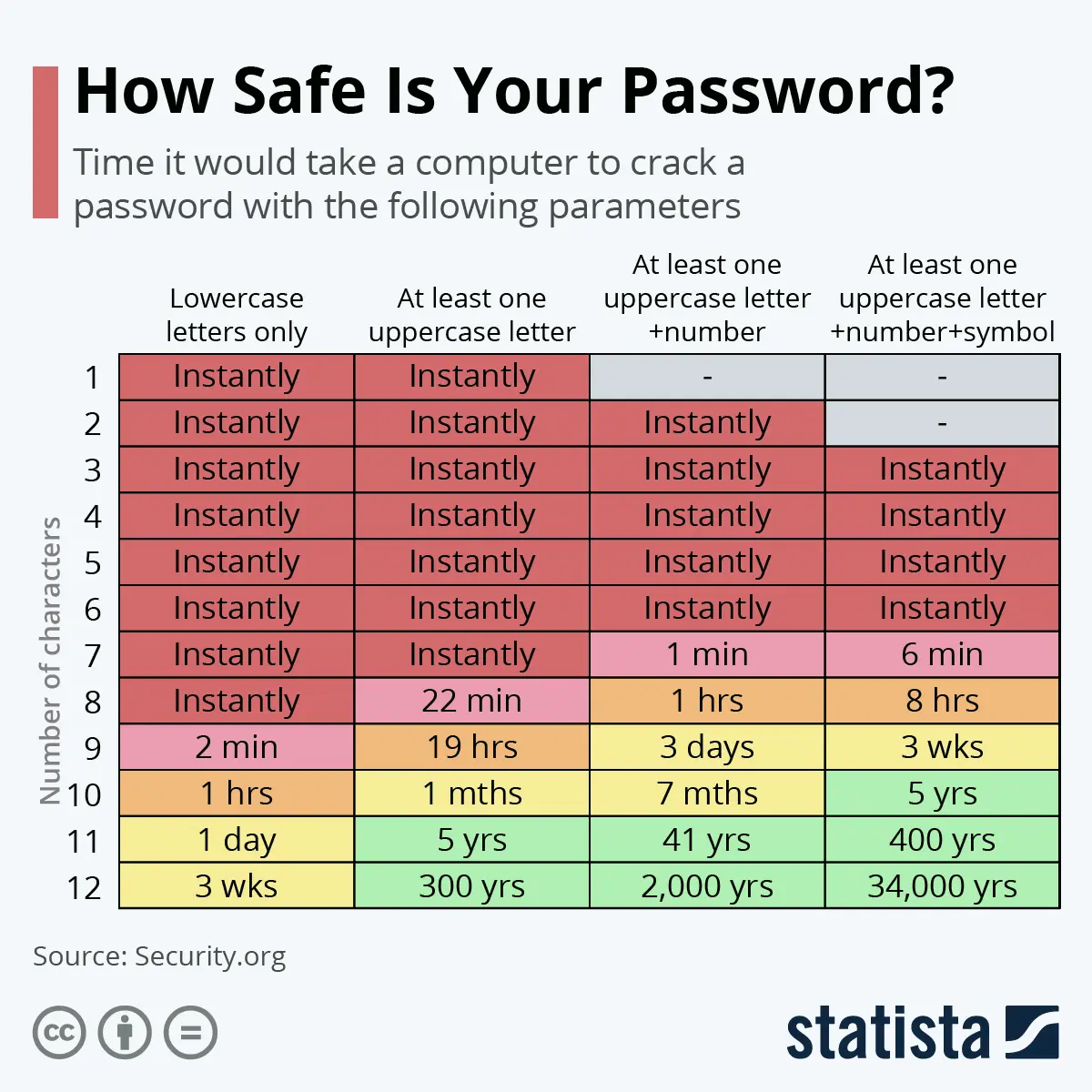
First, let’s take a look at how safe your current passwords are. In 2021, Statista created a chart detailing how long it takes to crack different types of passwords. Where do yours stand?
The message is clear: the most secure passwords are long and complicated.
But how do you keep up with them all? And how long should you use them? Is it okay to share your password with a trusted friend? How do you know if a password has been compromised?
First, the Do's:
- Do use a different password for every site you log in to. For instance, your work password should be completely different from your Netflix password.
- Do use two-or-more-step authentication (MFA). This means that beyond just requiring a password, a site will also send a secure code to your cell phone or email address, which you’ll then type into the log-in screen.
- Do use password management software (i.e. Dashlane or LastPass, etc.) to help you securely create, store, and manage passwords across all your devices.
- Do regularly check if your passwords have been compromised.
- Some companies, like Apple and Google, have this feature built in to their devices and apps, and will alert a user in the event of a security issue.
- To proactively check for breaches, use HaveIBeenPwnd (haveibeenpwned.com). On this site, users can anonymously and safely check the security of individual passwords and find out if their information has been part of any known data breach.
- Do change your password immediately, if you’re notified there’s been a security issue.
Now for the Don’ts:
- Don’t use personal information as your password, such as your date of birth or your social security number.
- Don’t use your user name as your password.
- Don’t recycle passwords. If you’ve used a password once, it’s done.
- Don’t leave your password written anywhere near your computer: on a sticky note, under your mouse pad, behind your monitor...
Your best defense against any kind of cyberattack is prevention, and that starts with a secure password.